
Ok Cool hires Alex Williamson as ECD of one billion dollars
OK cool completes the leadership team with two hiring of one billion dollars. #Cool #hires #Alex #Williamson #ECD #billion #dollars

OK cool completes the leadership team with two hiring of one billion dollars. #Cool #hires #Alex #Williamson #ECD #billion #dollars

If in fact the slowdown in productivity was caused at least partially by a fall in public spending on R&D, it is evidence that today we would be much richer if we had maintained a higher level of scientific investment. And also marks the dangers of today’s proposed cuts. “Based on our research,” says Fieldhouse,…

Protect your new iPhone 17 Pro or your new iPhone 17 pro max of scratches, scratches and falls with our favorite cases available for purchase now. The best cases for iPhone 17 Pro and iPhone 17 pro max If you want to make sure your new iPhone is well protected, we have compiled a complete…

For all music enthusiasts, Spotle is a super fun puzzle game where, instead of words, you use your musical knowledge to look for artists. While this may sound easy on paper, it is definitely not. I have spent hours trying to discover the answer, especially because there are no clues about your music. If you…

│ > The program doesn’t compile. Your shell g++ command didn’t work. The code actually │ uses Machin’s formula rather than Chudnovsky, even though a class that uses Chudnovsky │ is supplied. Where did you find this code? ✦ You’re right. Let me fix the code and properly implement the Chudnovsky algorithm, which is indeed…

Why can you trust techradar We spend hours trying all the products or services we review, so it may be sure that you are buying the best. Get more information about how we try. Genki Aegis Shield: Review The Genki Aegis Shield has a rather sublime homonym. In ancient Greek mythology, Aegis sometimes refers to…
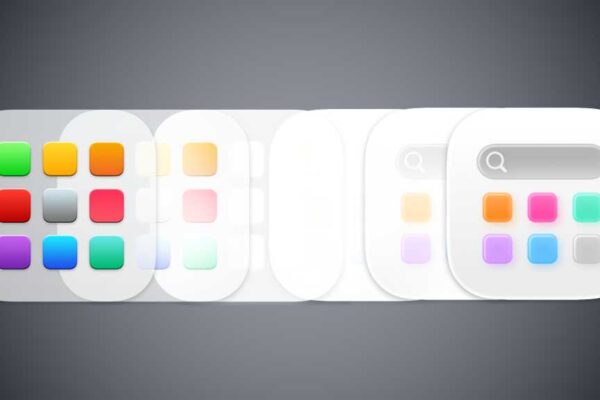
Launchpad had been part of the Mac operating system from OS X Lion, which was launched in 2011. After 14 years, LaunchPad is now retired, replaced by applications in Tahoe. Apps works a lot as the pitcher as a way to essentially access its application folder, but it has a new appearance and does not…

The Samsung Galaxy S25 Fe might seem almost identical to its predecessor, but there are small differences in the dimensions and improvements of much more significant specifications under the hood to separate the two. You cannot use S24 Fe cases in the S25 Fe, so if you plan to update it for its upper performance…
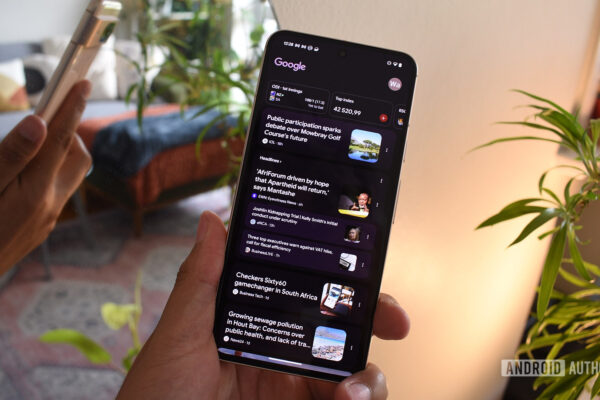
Andy Walker / Android Authority TL; Dr. Google Discover will soon show more content, including Instagram publications, X and YouTube shorts. Now you can follow creators and editors directly at Discover for a dedicated diet of their updates. Don’t forget to continue Android authority When we appear in your feed! For better or worse, Google…

British renewable energy supplier Octopus energy This week he said he is turning KrakenIts technological platform for public services, promoted in part for $ 500 million in annual revenues committed from other public services and energy suppliers. An IPO of eventual Kraken could be valued at $ 15 billion and could occur within a year,…