Computer pirates are hiding malware in a place that is largely beyond the scope of most defenses: Domain name system (DNS) system inside that assign the domain names to their corresponding numerical IP addresses.
The practice allows malicious scripts and early stage to obtain binary files without having to download them from suspicious sites or attach them to emails, where they are often put in quarantine by antivirus software. This is because Traffic for DNS searches often does not have monitoring for many security tools. While web and email traffic is often analyzed closely, DNS traffic largely represents a blind spot for such defenses.
A strange and lovely place
Researchers from Domaiindools on Tuesday saying Recently they saw the trick that was used to accommodate a malicious binary for Boke Screenmate, an annoying malware tension that interferes with the normal and safe functions of a computer. The file became the binary format in hexadecimal, a coding scheme that uses the digits 0 to 9 and the letters to a f to represent binary values in a compact combination of characters.
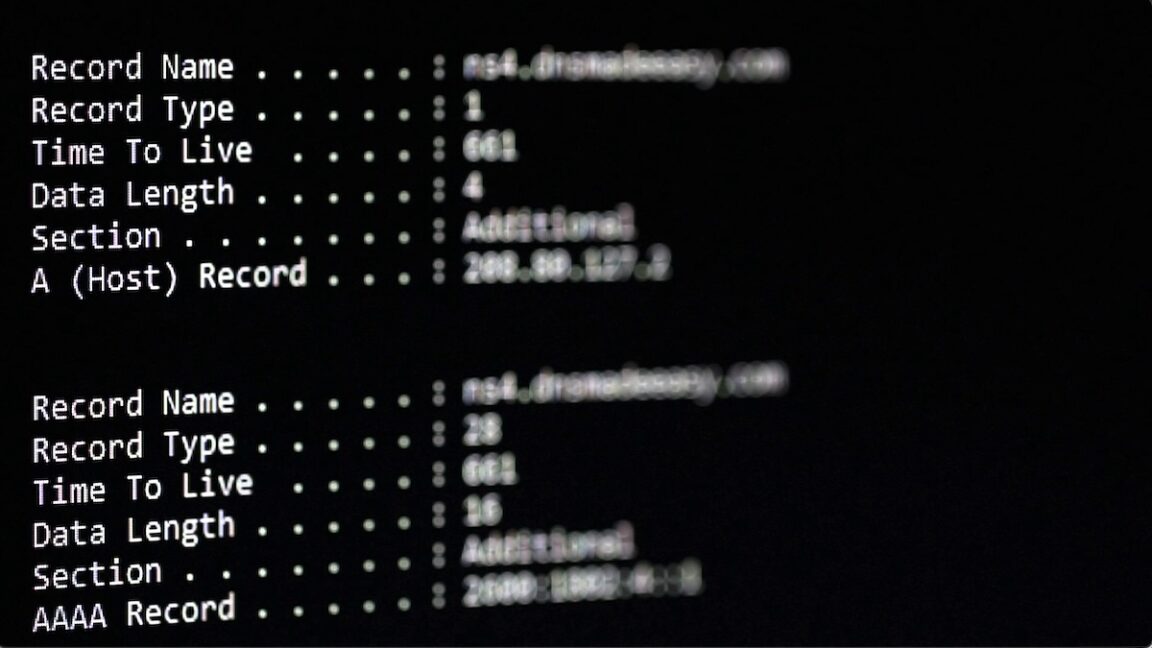
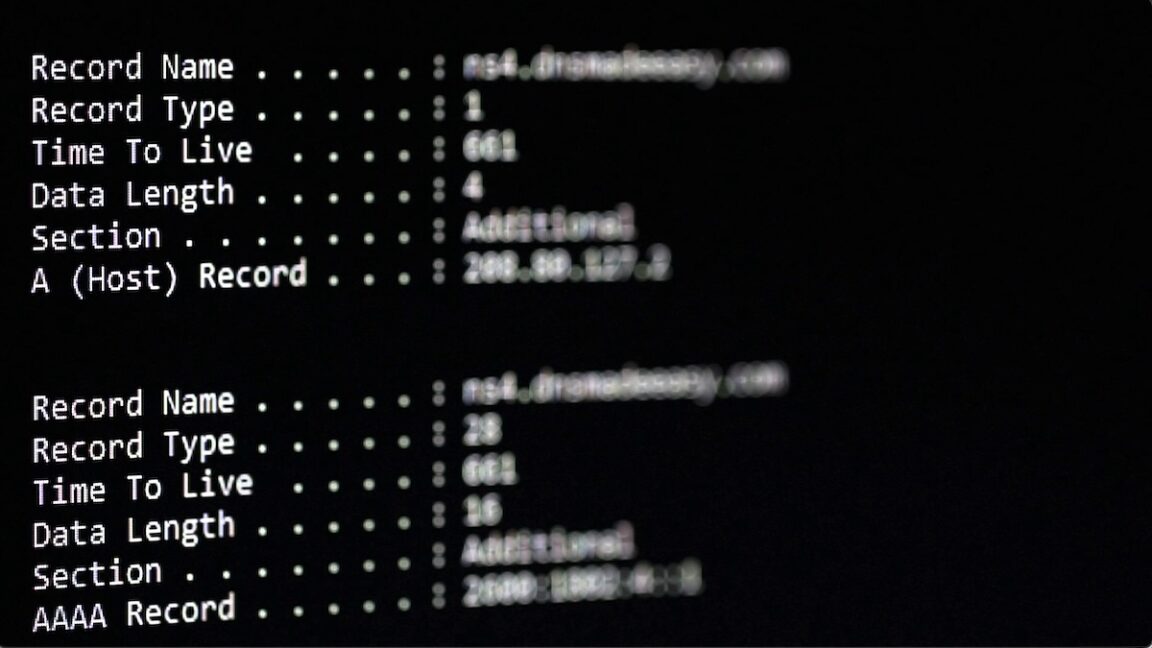
The hexadecimal representation was divided into hundreds of pieces. Each fragment was hidden within the DNS record of a different subdomain from the Whitetrective domain[.]com Specifically, the fragments were placed within the TXT record, a part of a DNS record capable of storing any arbitrary text. TXT records are often used to demonstrate the property of a site when configuring services such as Google Workspace.
An attacker who managed to put a finger on a protected network could recover each fragment using a series of innocuous appearance DNS applications, re -assemble them and then turn them into binary format. The technique allows malware to recover through traffic that can be difficult to monitor closely. As encrypted forms of IP search, known as DOH (DNS on HTTPS) and DOT (DNS on TLS), adoption gains, difficulty will probably grow.
#Computer #pirates #exploit #blind #spot #hiding #malware #DNS #Records

![[Botany • 2025] Thismia selangorensis (Thismiaceae) • A new mitriform species from the Thismia sect. Geomitra from Selangor, Malaysia](https://thenewshub.website/wp-content/uploads/2025/12/Thismia_selangorensis-novataxa_2025-Siti-Munirah_Siew-150x150.jpg)