In the last decade, Spyware tools have been repeatedly found in telephone numbers of journalists, activists and politicians, including US officials, raising concerns about the unprecedented proliferation of Spyware technologies and, subsequently, the lack of protections within the technological space amid threats.
Also: Google publishes a report from the person responsible while eliminating its commitment against weapons
Last Friday, Meta WhatsApp revealed that he had discovered a piracy campaign aimed at about 90 users, mostly journalists and civil society members in two dozen countries. According to a WhatsApp spokesman, the Israeli Spyware Company Paragon Solutions, now acquired by the Florida Private Capital firm, AE Industrial Partners, was behind the attack.
What is a zero click capacity?
It was discovered that Graphite, Paragon Spyware, had infiltrated WhatsApp groups simply by sending users a malicious PDF attached file. Without users’ knowledge, you can access and read messages in encrypted applications such as WhatsApp and Signal.
This is also known as a zero click attack, which means that the objectives do not have to take any measure for their devices to commit. On the contrary, Phishing or a single click attacks require the user’s interaction with a malicious link or an attached file. Once a phone is infected with a zero click capacity, the attack operator can secretly obtain total access to the phone exploiting a safety vulnerability.
Also: how to activate the private DNS mode on Android, and why it is essential for security
In an interview with ZDNET, Rocky Cole, co -founder of the mobile threat protection company, said that “in the case of Graphite, through WhatsApp, some type of payload, such as a PDF or an image, [was sent to the victims’ devices] and the underlying processes that receive and handle these packages have vulnerabilities that the attackers exploit [to] infect the phone. “
While public reports do not specify “if graphite can participate in the privilege escalation [vulnerability] And we operate outside WhatsApp or even moving to the Kernel iOS, yes, we know for our own detections and other works with customers, which it is possible that the escalation of privileges through WhatsApp to obtain access to the kernel, “Cole said.
Iverify has discovered instances in which “a WhatsApp series are blocked [mobile] devices [they’re] Iverify monitoring “has seemed to be malicious in nature, which leads to the Iverify team to believe that malicious attacks are” potentially more widespread “than only the 90 people who reported that they were infected by graphite.
While WhatsApp’s attack was predominantly launched against members of civil society, mobile spyware is an emerging threat against all because mobile exploitation is more widespread than one might think, Cole said. In addition, “the result is a Emerging ecosystem around Spyware mobile development And a growing number of mobile spyware companies supported by VC is “under pressure to become profitable companies,” he said.
Ultimately, this “creates marketing competition” for Spyware merchants and “reduces barriers” that would dissuade these mobile exploitation attacks.
Also: The 10 best brands exploited in Phishing attacks, and how to protect yourself
Just a month ago, WhatsApp He won a lawsuit Against NSO after a federal judge in California discovered that NSO was exploiting a security vulnerability within the messaging application to deliver Pegasus. The infamous NSO group, known for infecting the phones of journalists, activists and Palestinian rights organizations, has used similar click capacities through its Pegasus spy software with Israeli, a commercial spyware and telephone piracy tool.
Historically, the NSO group has avoided selling to customers based in the United States and has also been prohibited by the United States Department of Commerce under the Biden Administration for allegedly providing spyware to authoritarian governments. However, “changing political dynamics [under the Trump administration] It raises the possibility that the Spyware becomes more frequent in the United States “, exacerbating mobile exploitation.
“And the world is not fully prepared to deal with that,” Cole said.
Best practices to protect your device
Cole advises people to treat their phone as a computer. This means that, like one, “a body of best practices that exist to protect traditional final points such as laptop computers, exploitation and commitment, those same standards and practices should be applied to phones” would be applied. This includes restarting your phone daily because “many of these exploits exist only in memory. They are not files, and if your phone restarts, in theory, you should also be able to clean the malware,” he said.
Also: why you should turn off your phone once a week, according to the NSA
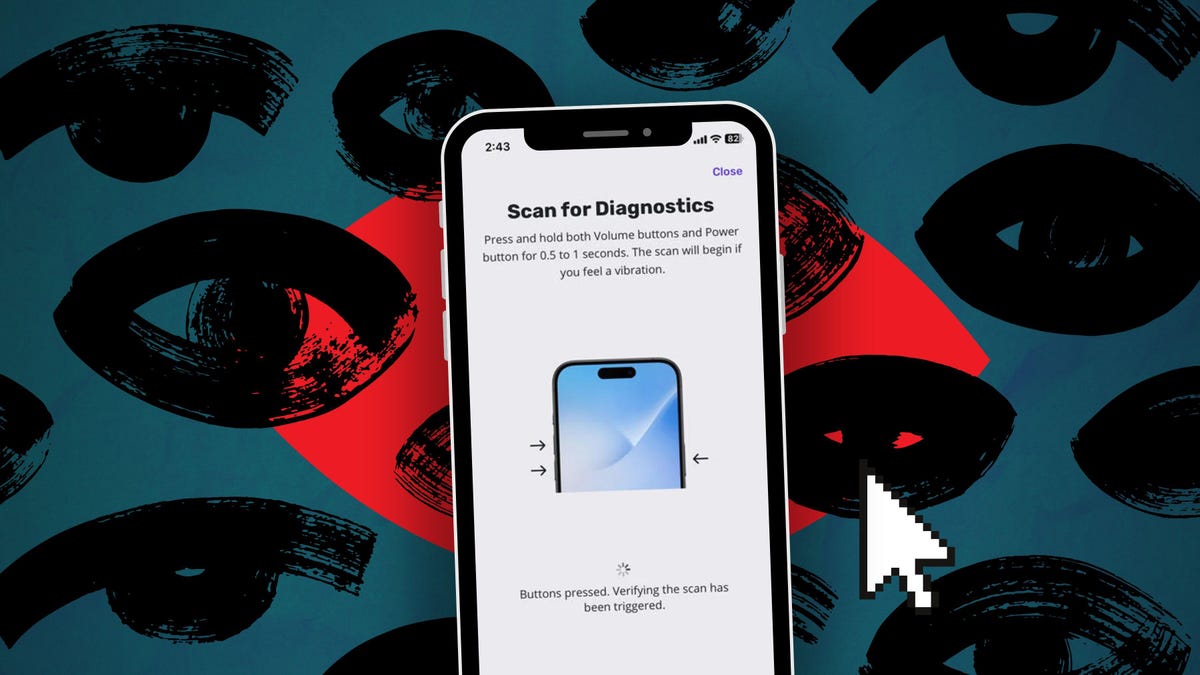
However, Cole also points out that if it is a zero click capacity such as Graphite or Pegasus, it can easily reinforce itself, so it is recommended to use a mobile security tool to know if it has been attacked. The Iverify mobile threat scanner for advanced mobile commitment costs only $ 1 and is easy to use. To learn to download and test the application for you, see our guide on how to detect the infamous spyware on your phone.
You can also try the block mode if you are using an Apple device. According to Cole, “blocking mode has the effect of reducing some functionality of Internet -oriented applications [which can] Somehow, reduce the surface of the attack to some extent. “
The only way to really defend against click zero capabilities is to fix the underlying vulnerabilities. As Cole emphasized, this means only Apple, Google and application developers can do that, “so, as an end user, it is vital that when there is a new safety patch available, apply it as soon as possible” .
#restart #phone #daily #defense #click #attacks